In the recently published 2022 Cyber Security Breaches Survey, an alarming 92 percent of higher education institutions reported breaches or attacks in the past 12 months.
This isn’t an isolated case. Even in 2020, the education sector experienced a total of 819 data breaches, according to Verizon’s Data Breach Investigations Report. Of this number, 228 have confirmed disclosure of private data.
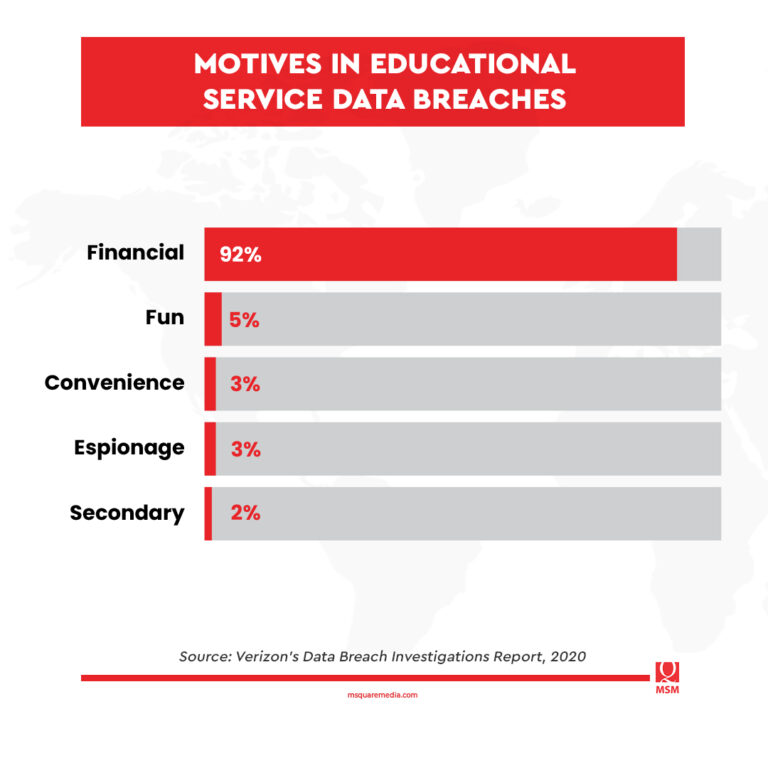
Based on the report, the threat actors were primarily financially motivated in 92 percent of the incidents. This means that they intend to sell the data—75 percent of which contain personal information—to interested buyers.
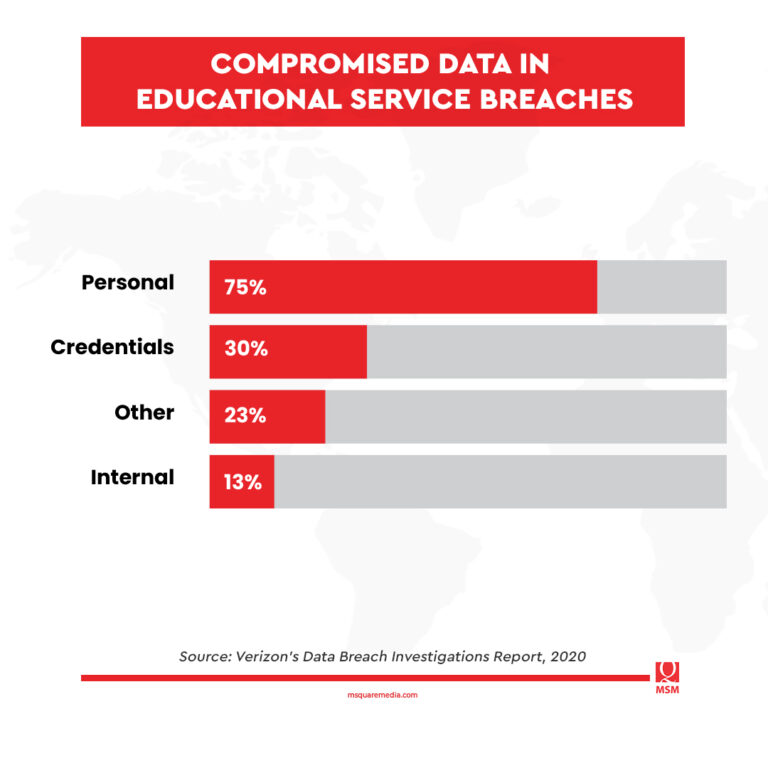
Cyber threat actors are particularly targeting the education industry. In fact, those behind the attacks would use social engineering tactics to siphon data from vulnerable targets.
For instance, email and data security company Mimecast revealed that colleges, private educational companies, and training providers were sent the most emails with malicious attachments during the first quarter of 2019.
In its Threat Intelligence Report, Mimecast suggested that professional education was primarily targeted because of the higher education institutions’ (HEIs) ambivalent positions of being open institutions of higher learning.
These findings echoed the findings of a 2017 survey, which revealed that as much as 50 percent of education-vendor sites do not have proper security measures, particularly support for encryption.
Most Common Security Risks in the Education Sector
When hackers get access to a college or university system, it can cause serious repercussions, including:
Financial Risks
Universities and educational companies can receive costly fines for allowing data breaches.
Back in 2016, the Personal Data Protection Commission, a Singapore-based software development organization working with learning institutions, received a penalty of S$60,000 (more than $45,300 in today’s money) for its failure to secure the personal information of close to 48,000 people.
On top of paying fines, institutions also have to spend their resources to repair the system and restore damages. In 2014, the University of Maryland had to shoulder $6 million for credit monitoring services after a hacking incident exposed the private information of nearly 310,000 past and current students, faculty, and staff.
Ransomware
Since most hackers are financially motivated to hack into systems, they can encrypt vital information to lock out users in exchange for millions of dollars.
In July 2019, the students, faculty, and staff of Monroe College in New York were locked out of their email, learning management system, and the college’s website. The hackers demanded $2 million in bitcoin as payment to restore access. Unfortunately, not all hackers restore access once they receive the ransom money.
System Manipulation
Hackers can use a teacher’s data to access the school’s system to manipulate admissions, change grades, and even cause reputational harm to the institution.
Data breaches in the education industry not only pose great security risks to the HEIs, but also cause a negative impact on the welfare of students and staff.
By getting enough personal information, hackers can use these details to access bank accounts, phone records, and even credit card information. In some cases, threat actors can use these sensitive data, including medical records, sexual orientation, and criminal information, to steal identities, as well as jeopardize relationships and career advancement.
GDPR and Student Information Safety: What Education Providers Should Know
In addition to security risks, education providers need to ensure that their data collection and storage comply with governing privacy laws.
The General Data Protection Regulation (GDPR) is a privacy law that has jurisdiction over entities that collect or process the personal data of European Union (EU) residents. This means that institutions that have international students in the EU need to comply with GDPR.
GDPR formed six principles to guide organizations when it comes to handling and processing personal data. It involves transparency, legitimacy, limitations, and adequacy of data.
For education technology providers, there must be explicit information about how data is collected and stored. Here’s how they can effectively comply with privacy laws:
1. Provide Information on Data Rules
Education providers must follow relevant privacy laws, including informing staff and students about the different data rules. They should also make sure that private data is accessible to the owners.
2. Collect Data With a Purpose
Data collection should be purpose-driven; HEIs should limit the use of data only for its intended purpose. All of the data in their systems cannot and should not be used for any other purpose other than initially stated without the owner’s consent.
3. Practice Minimum Data Collection
Education providers should only collect the least amount of data necessary to fulfill student requirements.
4. Maintain Accuracy of Systems
Data systems should be updated. Education institutions must address any errors and inaccuracies within one month of discovery.
5. Adhere to the Proper Disposal of Data
Education managers should also ensure proper data disposal when it is no longer needed. Old student data and files must be deleted from the system once they no longer serve their purpose.
6. Uphold Confidentiality
HEIs have a responsibility to do everything they can to keep the information safe and secure. They must use resources, including organizational and technical tools, to protect personal information from accidental loss, unauthorized access, and damage.
Takeaways
Compliance with data privacy policies may help protect student data. However, it should not be the only solution education providers should come up with. They must also ensure that their institution is 100 percent immune to identity theft, data breaches, and cyber-attacks.
Sources:
Gov.UK. “Cyber security breaches survey 2022.” Retrieved from: https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2022
Langlois, Philippe (2020). “2020 Data Breach Investigations Report.” Retrieved from: https://www.cisecurity.org/wp-content/uploads/2020/07/The-2020-Verizon-Data-Breach-Investigations-Report-DBIR.pdf

